Blockchain Privacy Technologies

The Challenge
Privacy is essential for ensuring the confidentiality, integrity, and security of data and transactions on the blockchain. Without adequate privacy protections, sensitive information such as financial transactions, personal data, and business contracts may be exposed to malicious actors, leading to privacy breaches, identity theft, or financial fraud. Privacy-enhancing technologies address these concerns by providing secure and confidential execution of transactions while still leveraging the transparency and immutability of the blockchain.
Fully Homomorphic Encryption (FHE) represents a breakthrough approach to blockchain privacy, enabling computations directly on encrypted data without ever decrypting it. This article explores FHE’s application in blockchain privacy protection, with Zama’s fhEVM protocol as a leading example, followed by a brief overview of alternative technologies.
Zama’s fhEVM Protocol
Zama’s fhEVM (Fully Homomorphic Encryption Virtual Machine) is a framework that integrates Fully Homomorphic Encryption (FHE) into Ethereum Virtual Machine (EVM)-compatible blockchains. It enables confidential smart contracts, where computations occur on encrypted data without decryption, preserving privacy while maintaining blockchain composability and verifiability.
Key guarantees include:
- End-to-end encryption of transaction inputs and contract states.
- No exposure of sensitive data to nodes, validators, or observers.
- Seamless integration with existing Solidity tools and EVM ecosystems.
fhEVM forms the core of Zama’s Confidential Blockchain Protocol, a layer that adds privacy to public blockchains without requiring chain modifications.
Technical Architecture
The fhEVM protocol is built on TFHE-rs, Zama’s open-source Rust implementation of Torus Fully Homomorphic Encryption, and supports the heavy encrypted data computation in off-chain coprocessors.
Symbolic Execution
The fhEVM protocol adopt the Coprocessor Model — Designed for Ethereum and Layer 2 networks:
- Symbolic Execution — The host chain handles logic but defers FHE operations, emitting events with encrypted handles instead of performing heavy computations.
- Off-Chain Computation — Specialized coprocessor nodes process FHE operations off-chain and return encrypted results via a Gateway contract.
- On-Chain Verification — Results are posted back to the host chain using a defense-in-depth approach combining threshold MPC and optimistic security (fraud proofs).
- Hardware Security — Coprocessor nodes utilize AWS Nitro Enclaves (Trusted Execution Environments) to ensure node operators cannot access key shares in memory.
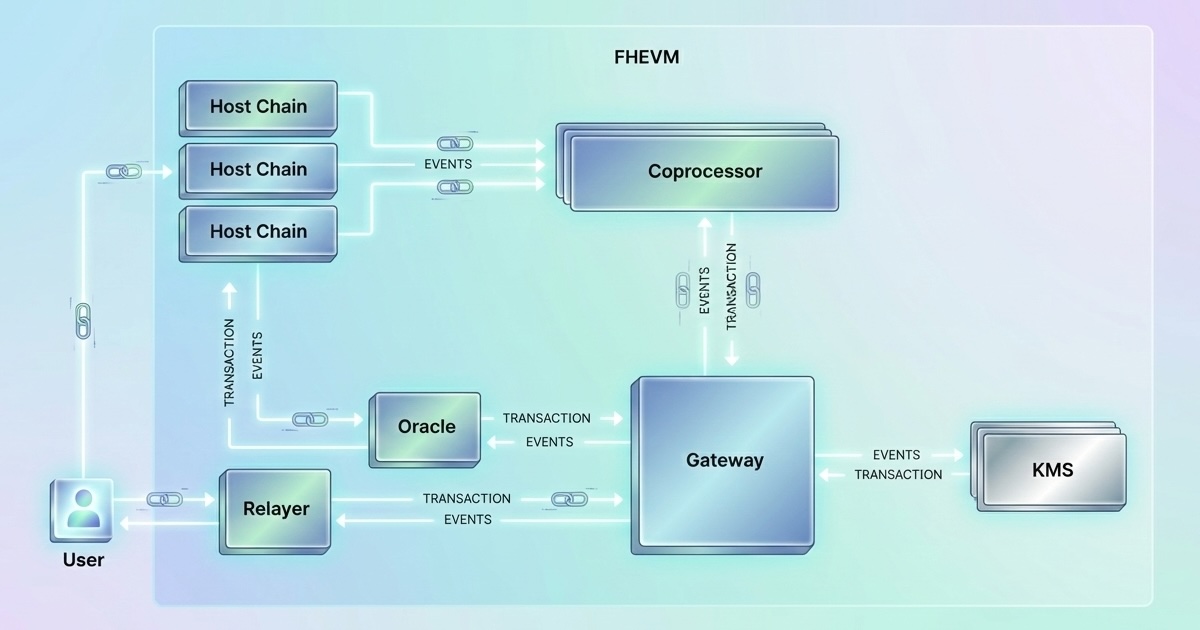
Key Management System (KMS)
The network private key is split among multiple validators using Threshold MPC—no single entity holds the complete key. Decryption requires supermajority consensus (e.g., 2/3 of nodes), ensuring no single party can decrypt user data unilaterally. Private (user-only) decryption re-encrypts results under the user’s key.
Encrypted Types and Operations
Supported encrypted types include ebool, euint8, euint16, euint32, euint64, euint128, euint160, and euint256. Available operations on ciphertexts include:
- Arithmetic: Addition, subtraction, multiplication, division (experimental)
- Bitwise: AND, OR, XOR
- Comparison: Equal, greater than, less than
- Transfer:
FHE.transferfor moving encrypted token balances
Developers write contracts in standard Solidity, importing the pre-compiled and deployed fhEVM library (formerly TFHE, now rebranded to FHE)—no cryptography expertise needed.
Recent Updates
The protocol has seen rapid iteration with key updates from v0.7 (July 2025) through v0.9 (October 2025):
- Library Rebranding — The Solidity library was renamed from
TFHEtoFHEto standardize the developer experience across the ecosystem. - Input Re-randomization — To prevent tracking users via ciphertext metadata, all transaction inputs are now automatically re-randomized before execution.
- Gas Optimizations — Significant reductions in gas costs for FHE operations, making confidential contracts economically viable on public testnets.
- Access Control Logic — Introduction of granular permissions (
FHE.allowandFHE.allowTransient) to strictly control who can view (decrypt) specific data fields, preventing unauthorized data leakage.
Project Timeline and Milestones
| Timeline | Category | Milestone | Details |
|---|---|---|---|
| March 2024 | Funding | Series A Round | Raised $73M (co-led by Multicoin Capital and Protocol Labs) |
| June 2025 | Funding | Series B Round | Raised $57M (co-led by Pantera Capital and Blockchange); achieved unicorn status |
| July 2025 | Testnet | Public Launch | Testnet v0.7 launched with Zama Protocol and Gateway components |
| September 2025 | Testnet | Version Update | Testnet v0.8 released |
| October 2025 | Testnet | Version Update | Testnet v0.9 released with state resets and enhancements |
| December 2025 | Testnet | Activity Milestone | Over 1.2 million encrypted transactions processed on testnet |
| Late 2025 | Testnet | Final Release | fhEVM v0.10 - Final testnet release focusing on stability and API freeze for mainnet |
| Q4 2025 | Mainnet | Ethereum Launch | Official mainnet launch of fhEVM Coprocessor on Ethereum |
| January 12-15, 2026 | Token | $ZAMA Auction | Sealed-bid Dutch auction for fair, private bidding using FHE; 10% of supply (1.1 billion tokens) via community distribution |
| January 20, 2026 | Token | Token Claim | Token distribution begins; no vesting, immediate liquidity |
| H1 2026 | Mainnet | EVM Expansion | Deployment to Arbitrum, Optimism, Base, and BSC |
| H2 2026 | Mainnet | Solana Support | Expansion beyond EVM to Solana Virtual Machine (SVM) |
| Ongoing | Infrastructure | Hardware Acceleration | Development of FHE ASICs to increase throughput from ~20 TPS to 1,000+ TPS |
Development and Ecosystem Activity
- GitHub Repositories — Highly active (e.g., zama-ai/fhevm with thousands of stars/forks). Includes Solidity libraries, Go integrations for EVM chains, Hardhat templates, and coprocessor backends.
- Community and Developer Engagement — Strong momentum. Developers actively build and test confidential DeFi, voting, gaming, and identity apps. Recent X discussions highlight smooth developer experiences, low latency, and real-world demos (e.g., confidential transfers, blind auctions).
- Use Cases Demonstrated — Confidential lending/borrowing, private token swaps, blind auctions, on-chain gaming strategies, and encrypted governance voting.
- Strategic Partnerships — OpenZeppelin collaboration produced the Confidential Token Standard, a privacy-preserving equivalent of ERC-20, audited for institutional-grade security in dark pools and private assets. Google Cloud partnership accelerates FHE operations using specialized hardware support.
Developer Experience
Zama’s primary competitive advantage is ease of use. Unlike Zero-Knowledge (ZK) applications that require complex circuit generation and asynchronous proving, fhEVM enables developers to write synchronous code using standard tools:
- Tooling — Fully compatible with Hardhat and MetaMask. Developers can use standard Solidity tools. A Foundry template is scheduled for Q1 2025.
- Mental Model — Write code that looks like standard Solidity:
function add(euint32 a, euint32 b) public view returns (euint32) {
return FHE.add(a, b); // Computed on encrypted data
}The gas cost is comparatively much higher than the plaintext type. For example, a euint256 typically cost 32000 gas.
Future Outlook
fhEVM positions Zama as a leading “confidentiality layer” for blockchains, enabling privacy-preserving DeFi, AI, and identity without sacrificing composability. Mainnet and token launch in late 2025/early 2026 are major catalysts. Community programs (e.g., Creator Program Season 5) and testnet participation drive pre-mainnet adoption.
In summary, fhEVM is production-ready on testnet, with rapid progress toward a transformative mainnet deployment that could redefine blockchain privacy.
Other FHE-Based Solutions
Zama’s fhEVM has successfully positioned itself as the underlying engine for the confidential blockchain sector. The FHE ecosystem is growing rapidly in 2025, driven by hardware advances and demand for encrypted computation:
| Project | Category | Description |
|---|---|---|
| Inco Network | fhEVM-Dependent | Modular confidential computing L1 powered by Zama’s fhEVM stack (native integration model). EVM-compatible layer focused on gaming, RWAs, and identity, positioning as universal web3 confidentiality-as-a-service via IBC/messaging. |
| Fhenix | fhEVM-Dependent | L2 (and potentially L1) powered entirely by Zama’s fhEVM stack (native integration model), providing confidential contracts on Ethereum with similar symbolic execution approach. |
| Shiba Inu | fhEVM-Dependent | One of the largest tokens by market cap, using the fhEVM to build an entire network state for their community, powering everything from their decentralized financial infrastructure to their metaverse. |
| Sunscreen | Independent | FHE compiler/tooling for privacy apps; supports cross-chain dApps (Rust-based). |
| Mind Network | Independent | FHE rollup for private data; zero-trust focus. |
| Octra | Independent | Isolated FHE environments. |
| OpenFHE | Independent | Emerging tools and integrations. |
Alternative Privacy Technologies
While FHE offers powerful capabilities for programmable privacy, other cryptographic approaches also play important roles in blockchain privacy:
Comparing FHE vs. ZKP vs. MPC in Blockchain Privacy
| Aspect | FHE (e.g., Zama fhEVM) | ZKP (e.g., zk-SNARKs/STARKs) | MPC (e.g., Threshold Schemes) |
|---|---|---|---|
| Core Strength | Arbitrary computation on encrypted data | Proof of knowledge without revelation | Joint computation across parties |
| Privacy Level | End-to-end (data always encrypted) | Selective (hides specifics, proves validity) | Input privacy during collaboration |
| Composability | High (encrypted state interoperable) | Medium (limited by circuit design) | Medium (requires party coordination) |
| Performance | Improving but computationally intensive | Fast verification; proof generation varies | Efficient for specific tasks (e.g., signing) |
| Verifiability | Publicly verifiable operations on ciphertext | Succinct proofs for on-chain verification | Verifiable if combined with proofs |
| Trust Assumptions | Threshold key management (often MPC-aided) | Trusted setup (some schemes) or none | Honest majority/threshold |
| Use Cases | Confidential DeFi, private smart contracts | Private transactions, scaling rollups | Secure wallets, RNG, cross-chain bridges |
| Maturity (2025) | Rapid growth; mainnets emerging | Mature; dominant in scaling/privacy | Established for niche (e.g., wallets) |
| Drawbacks | High overhead; emerging hardware acceleration | Circuit constraints; proof size/time | Communication overhead; party availability |
Zero-Knowledge Proofs (ZKP)
ZKP proves statements (e.g., transaction validity) without revealing underlying data, ideal for selective disclosure and verifiability. ZKP dominates privacy and scaling, powering private transactions and confidential contracts through mature implementations. Notable projects include Aztec Network (Ethereum ZK-Rollup for private smart contracts), Aleo (Layer-1 with ZKP-native smart contracts via Leo language, partnering with Circle for private USDCx stablecoin), Mina Protocol (lightweight Layer-1 using recursive zk-SNARKs), and established privacy coins like Zcash (shielded transactions, 2025 market surge) and Monero (ring signatures + ZKP elements). ZKP projects lead in adoption due to maturity and scalability integration (e.g., zk-Rollups).
Multi-Party Computation (MPC)
MPC allows multiple parties to jointly compute functions over private inputs without exposing them, excelling in threshold cryptography and collaborative privacy. MPC is widely used for key management and threshold operations. Key implementations include Secret Network (Cosmos-based chain with secret contracts using TEEs + MPC elements for confidential DeFi/voting), ARPA Network (permissionless MPC network for verifiable RNG, secure wallets, and bridges), Partisia Blockchain (native MPC for general-purpose secure computation, combining with FHE), and threshold applications in wallets (e.g., TSS in multi-sig). MPC often augments other technologies, such as threshold decryption in FHE systems like Zama’s.
Trusted Execution Environments (TEE)
TEE provides hardware-based isolated execution environments for confidential computation. While not purely cryptographic, TEEs complement cryptographic approaches in privacy solutions. Secret Network notably combines TEEs with MPC elements to enable customizable privacy via secret contracts.
Current Landscape and Trends
Privacy is crypto’s hottest narrative in December 2025: Institutional adoption surges (e.g., tokenized assets need confidentiality), regulatory clarity emerges (e.g., U.S. acts supporting compliant privacy), and market performance reflects growing demand (Zcash +1172% YTD).
Hybrid approaches dominate the landscape, with protocols combining ZKP (verifiability), MPC (key management), and FHE (computation) to balance trade-offs. While regulatory pressure on “absolute” privacy causes some delistings, focus shifts to compliant tools that can be audited by authorities when necessary.
Looking forward, privacy technologies enable mainstream use cases including private DeFi, identity management, and AI on-chain. ZKP leads in scaling solutions, FHE pioneers programmable privacy, and MPC provides secure collaboration infrastructure. The space is converging on hybrid solutions for balanced privacy, composability, and compliance.